Working in a security environment you get used to dealing with threats. One day we get this email forwarded to us by a colleague who received via a secure email address that is reserved for clients.
It was the one email. For the purposes of this story, it should be noted that we don’t have a bug bounty program. That is important for the story, but not a topic I’m covering. However this was peculiar because of how the email was received and what was in it.
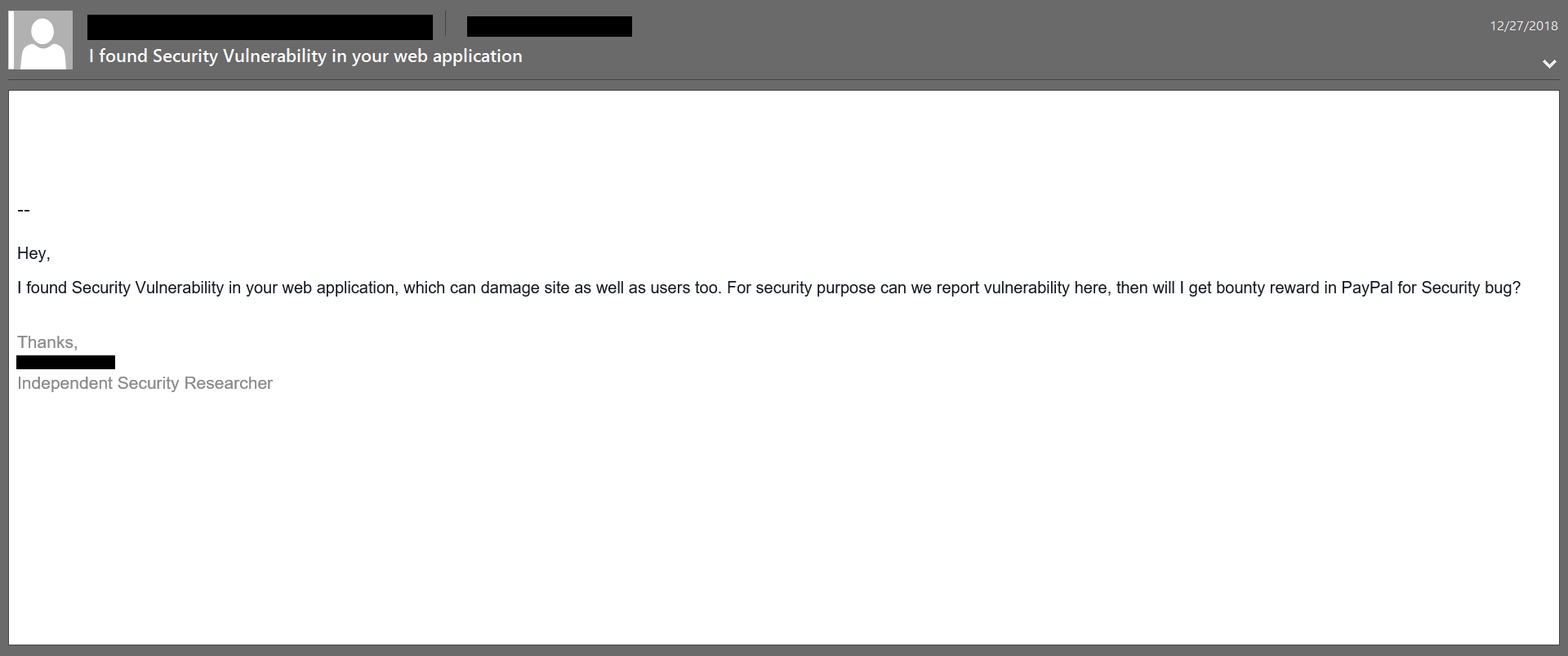
This is the wrong approach for several reasons. The email was vague and sent through a a secure email address or one that is only given out to clients. They gave no explanations on how they got that address. The sender wanted to continue communications without verifying who they were. Afterwards they wanted/demanded payment for their reporting through Paypal.
It should also be noted that this is not to make fun or poke holes at the individual, but to highlight the issue with a method like this.
Do not communicate with them through whatever exploit or vulnerability you found. This is highly unethical and a violation of the Computer Fraud and Abuse Act. Not to mention, all goodwill and trust is gone before communications take place. This is the equivalent of breaking into someone’s home and telling them their house is unsecured while offering to fix it for them.
If a company does not have a have an active bug bounty program or any identifiable ways to message them. There are many ways to approach it without.
- Reach out through their official contact forms or numbers
- If you can find one of their security team members on Linkedin and them an email letting them know. Politeness is key as they don’t know who you are.
- Reach out through social media and let them know you have something important. Again, make sure to be polite and give them a general idea what you have.
To sum up, bug bounties are a great way to find and patch vulnerabilities and exploits while also making some money on the side. If you find a vulnerability or exploit and the company in question does not have a bug bounty program, do not reach out to them through that vulnerability or exploit. There are other ways to let them company know. If you are doing it purely for money, move on to something easier and better to report on.
If you like the blog, help support me on ko-fi.
[kofi]